Getting Started
Getting Started
The Devdraft Console is a web-based interface for managing payments, products, and integrations without writing code.
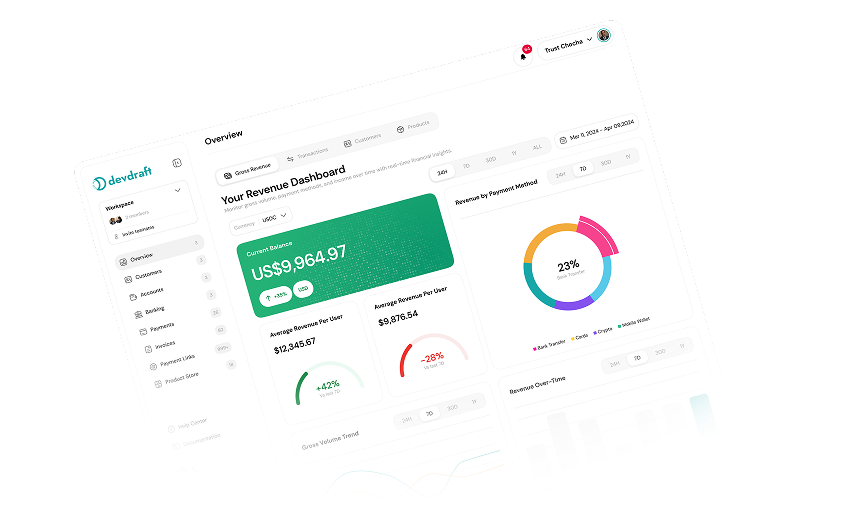
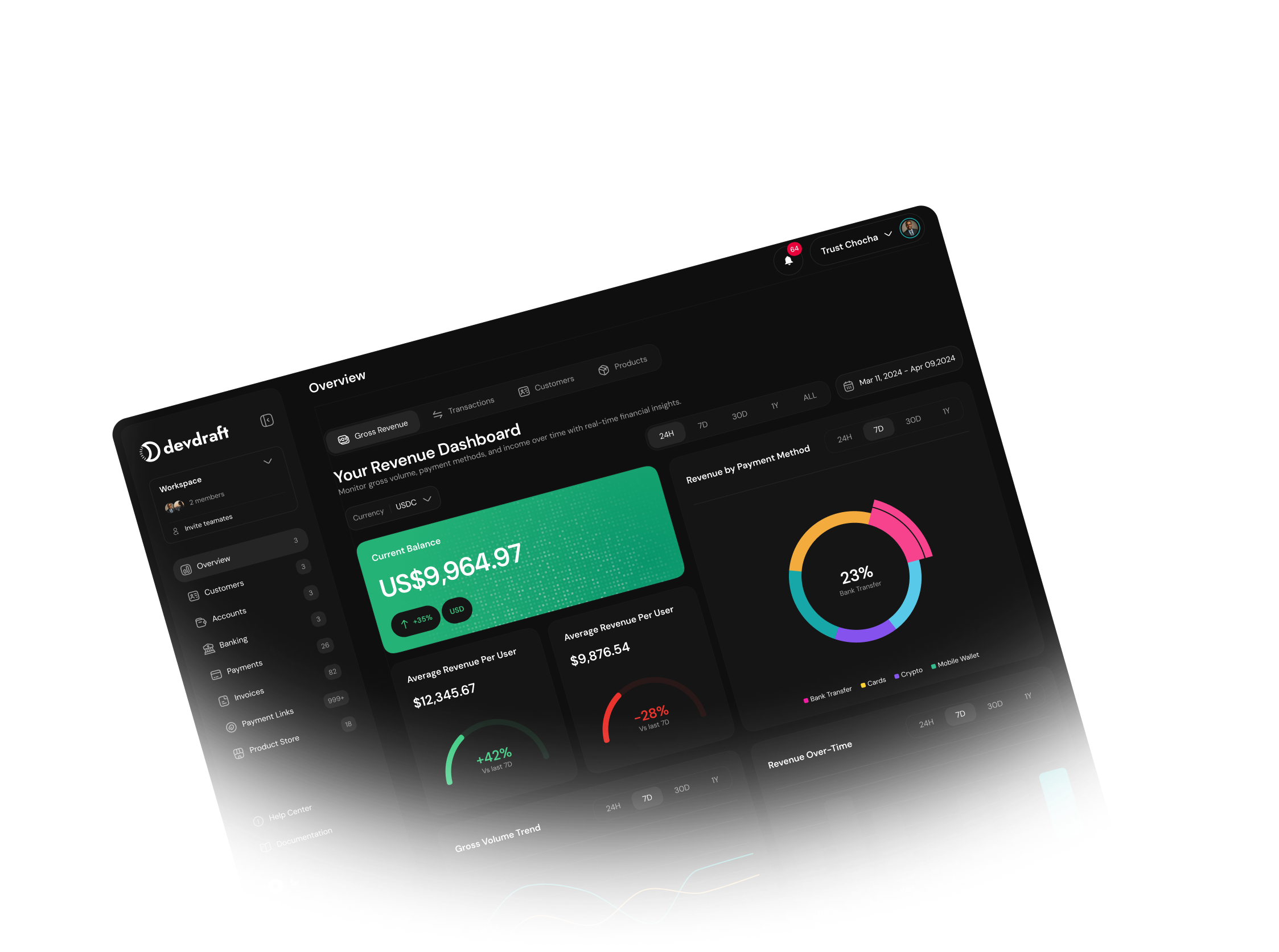
Accessing the Console
1
Navigate to Console
Visit console.devdraft.ai in your web browser.
2
Sign In
Use your Devdraft account credentials or create a new account.
If you’re part of an organization, you may need an admin invitation first.
3
Complete Setup
Follow the guided setup to configure your organization details.
Account Setup
Organization Information
1
Update Organization Details
Navigate to Settings → Business Details:
- Organization name
- Contact email
- Logo and branding
2
Configure Contact Information
Add support details visible to customers during checkout.
Key Features to Explore
Account Verification
Complete KYC verification to unlock all features.
API Keys
Generate and manage your API keys for integrations.
Payment Links
Create payment links for easy customer transactions.
Product Store
Set up your digital and physical products.
Authentication & Security Setup
Configure additional security measures and authentication options for your account.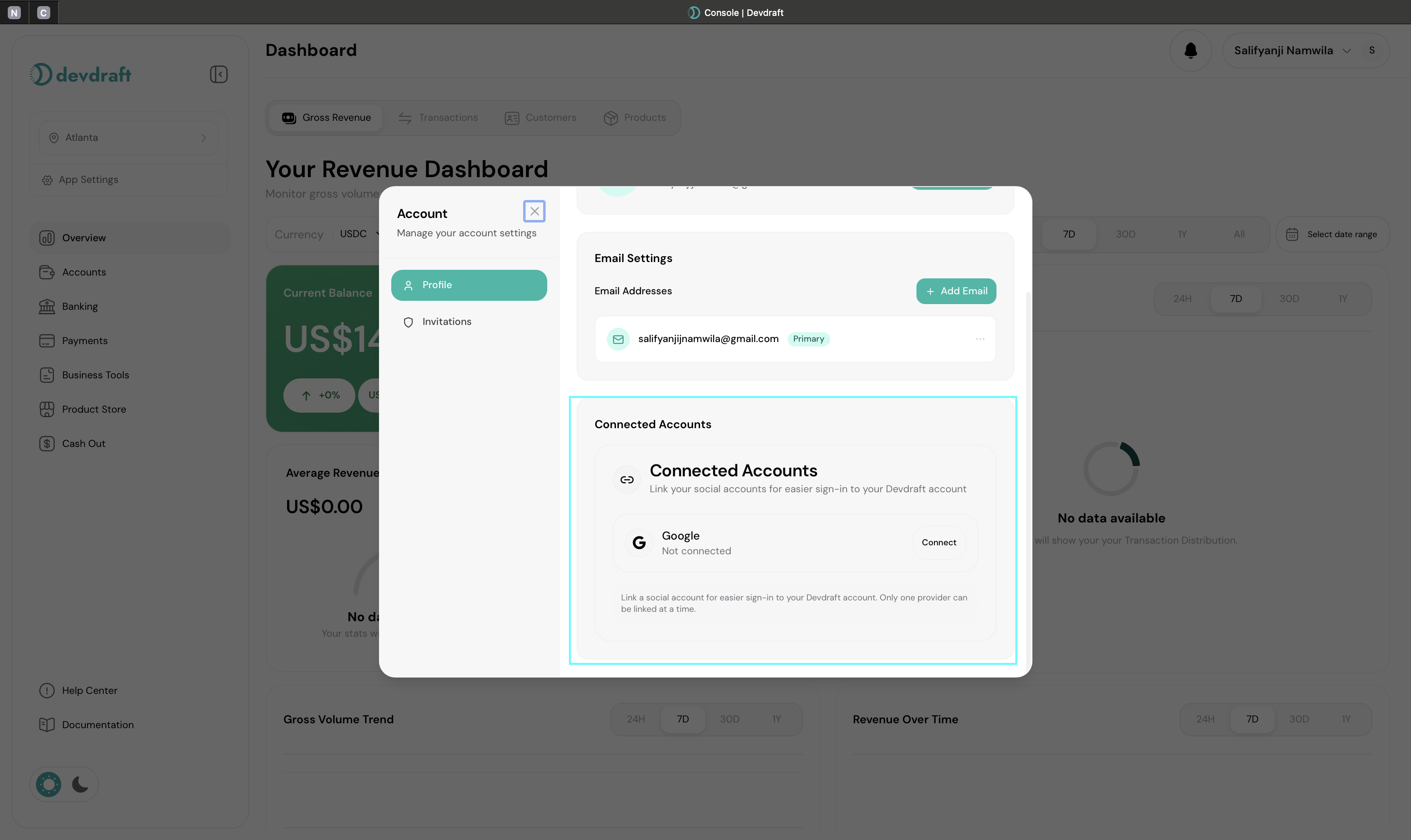
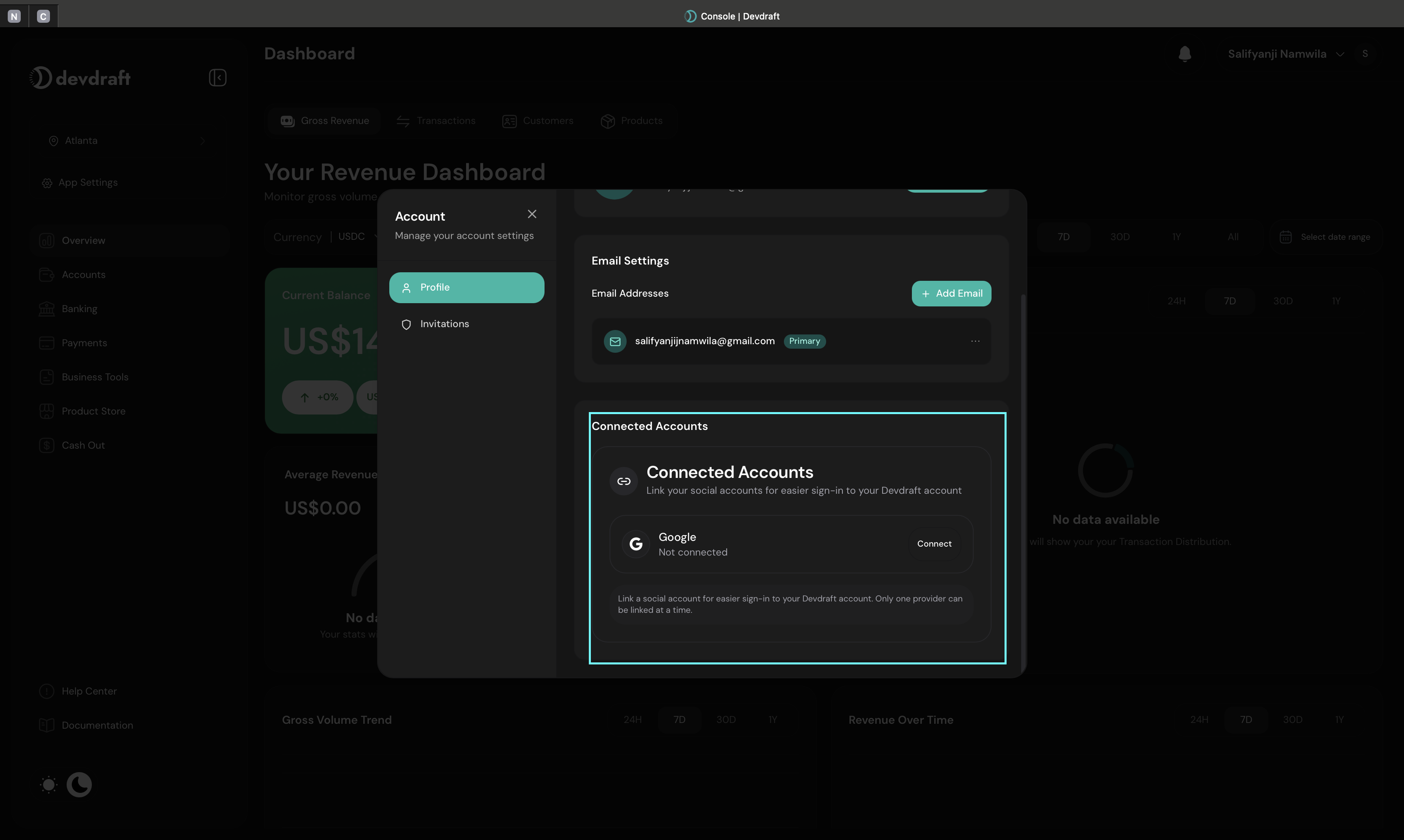
Google Sign-In Integration
Need help? Contact support at support@devdraft.ai or visit our FAQ.

