Create completely customizable roles by selecting individual permissions atomically. Each role is built from granular permissions that you choose specifically, allowing you to craft precise access control that matches your exact business needs and team responsibilities.
What are Roles?
Create completely customizable roles by selecting individual permissions atomically. Each role is built from granular permissions that you choose specifically, allowing you to craft precise access control that matches your exact business needs and team responsibilities.
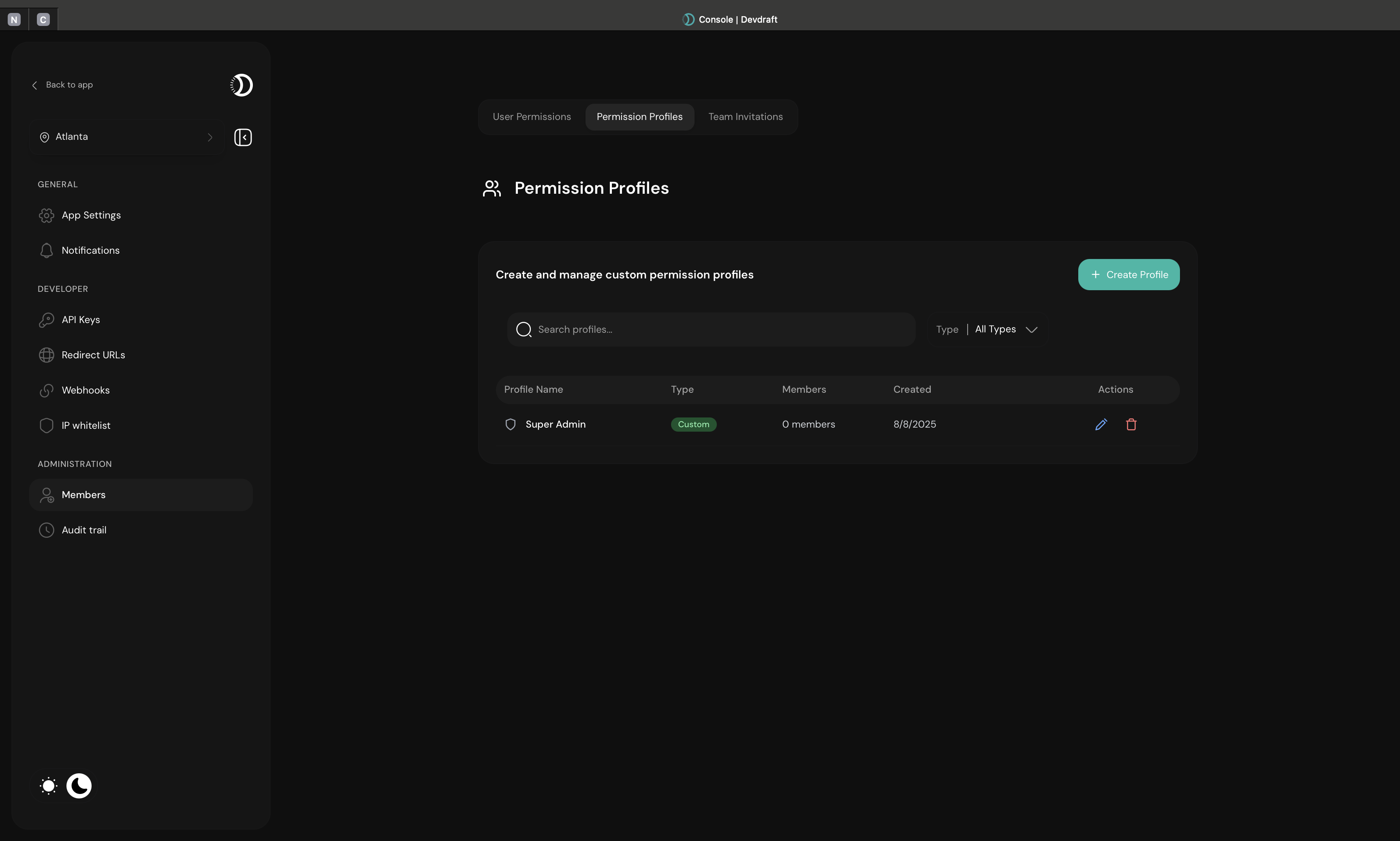
Permission Profile Overview
Quick Setup
Create your first custom role in under 3 minutes:1
Access Role Management
Navigate to Team → Roles in your dashboard
2
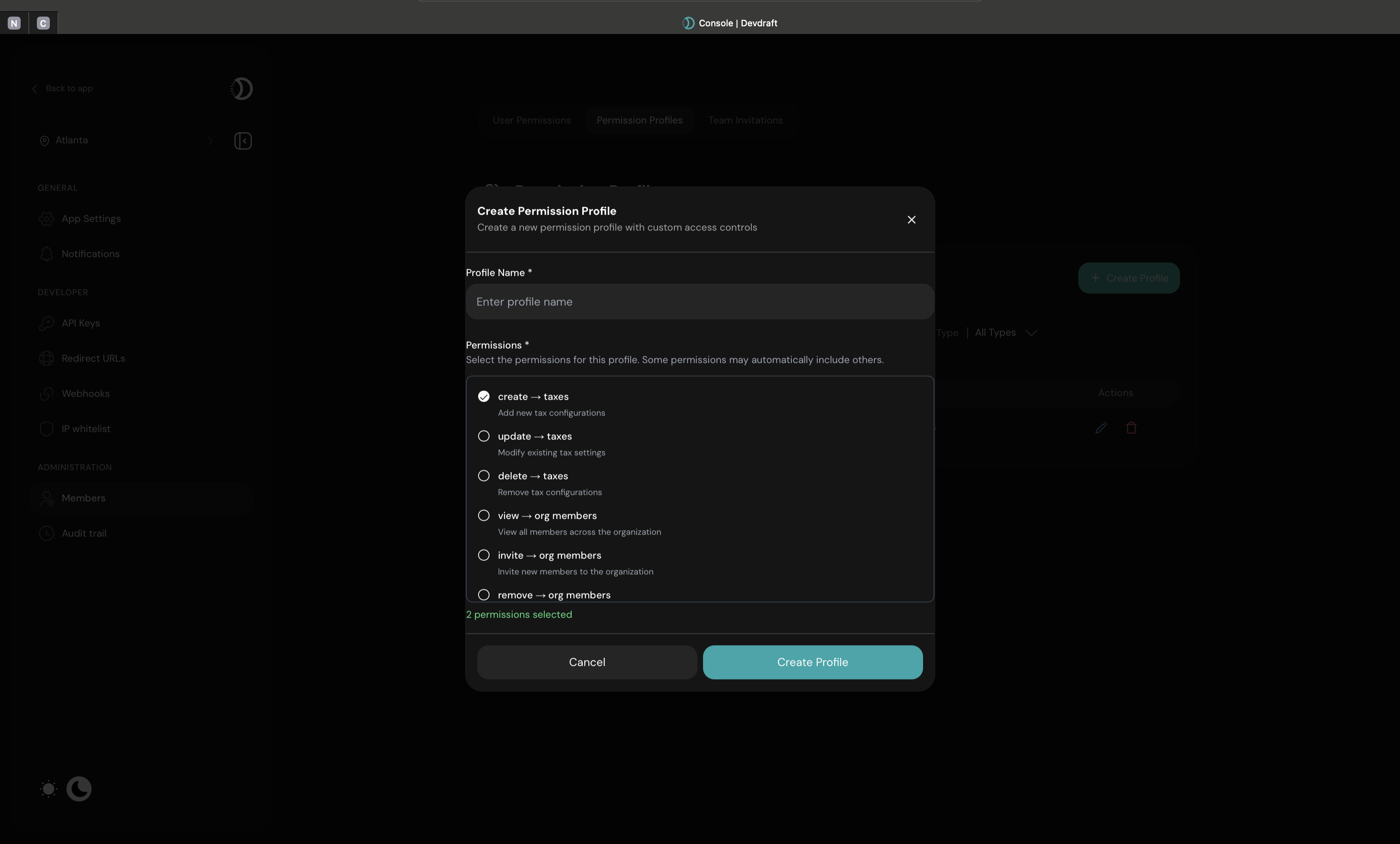
Create Custom Role
Click Create Permission Profile and configure role details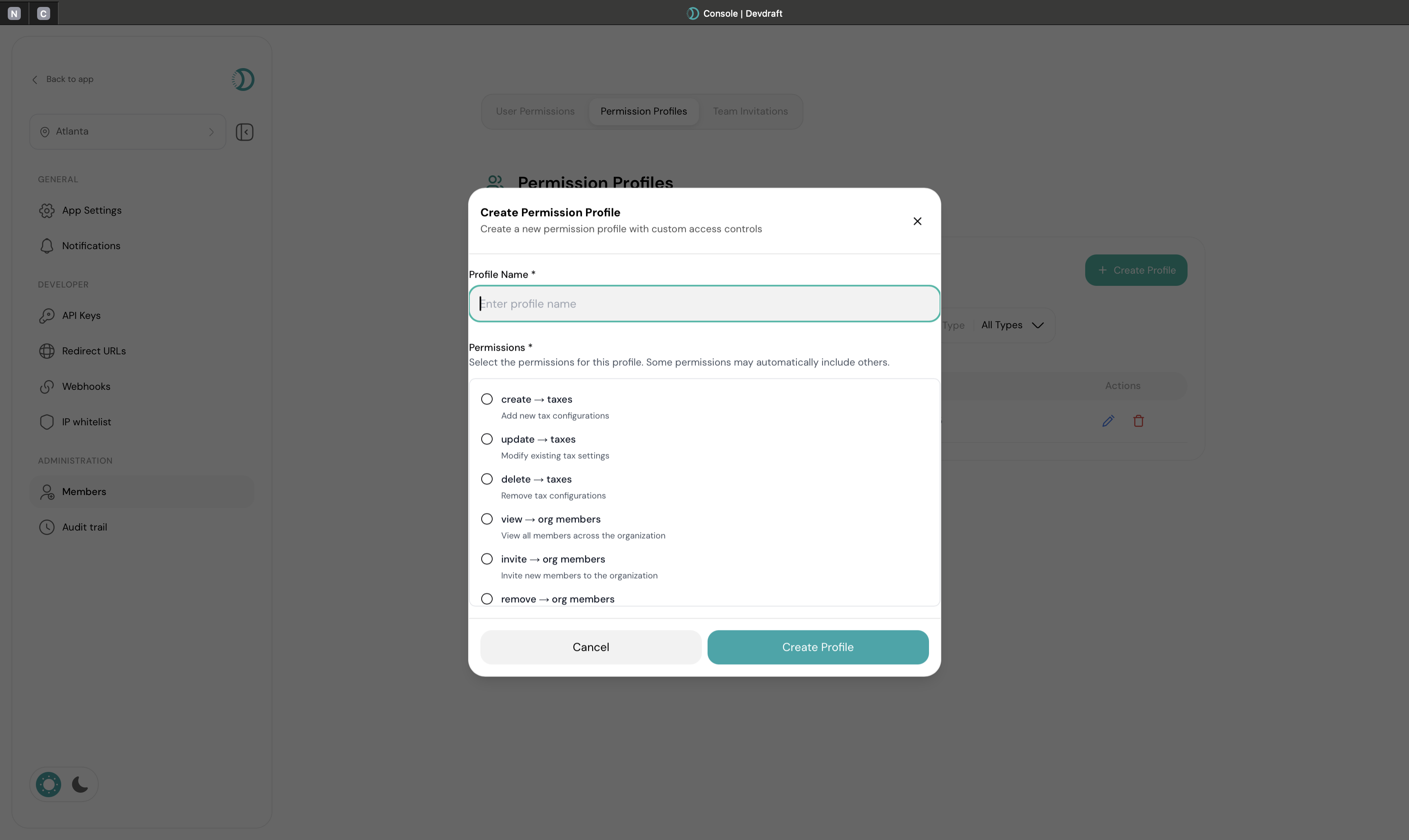

Create Permission Profile Interface
3
Define Role Details
Enter role name and description
4
Configure Permissions
Select specific permissions for the role
5
Save and Assign
Create the role and assign it to team members
System Roles vs Custom Roles
- System Default Roles
- Custom Roles
Pre-Built System Roles:Devdraft includes only two system-defined roles that you cannot modify:
- Super Admin: Complete system access and configuration
- Full administrative privileges
- Cannot be customized or deleted
- System-level access control
- Authorized Representative: Legal compliance role
- Automatically assigned to the account creator
- System-reserved for regulatory requirements
- Cannot be modified or deleted
- Used for legal and compliance purposes
Creating Custom Roles
1
Access Role Management
Navigate to Team → Roles in your dashboard
2
Create Custom Role
Click Create Permission Profile and configure role details

Create Permission Profile Interface
3
Select Atomic Permissions
Permission Selection:
- Choose individual permissions from categories
- Build custom access levels
- Apply principle of least privilege
- Test permission combinations
4
Save and Deploy
Save your custom role and assign it to team members.
Managing Existing Roles
View All Roles
View All Roles
Role Overview:
- All custom and system roles
- Permission summaries
- Assignment statistics
- Usage patterns
- Edit role permissions
- Clone existing roles
- Delete unused roles
- Assign roles to users
Edit Role Permissions
Edit Role Permissions
Modify Existing Roles:
- Add new permissions to roles
- Remove unnecessary permissions
- Update role names and descriptions
- Adjust permission dependencies
1
Select Role to Edit
Find the role you want to modify from the roles list.
2
Update Permissions
Add or remove permissions based on changing needs.
3
Save Changes
Apply updates to affect all users with this role immediately.
Duplicate Roles
Duplicate Roles
Create Similar Roles:
- Copy existing role as starting point
- Modify permissions for new requirements
- Maintain consistent naming conventions
- Save time on similar role creation
- Regional variations of the same role
- Different permission levels for similar positions
- Temporary project-specific roles
- Department-specific modifications
Delete Roles
Delete Roles
Role Removal:
- Only delete unused roles
- Reassign users before deletion
- Cannot delete roles with active assignments
- Permanent action that cannot be undone
1
Check Role Usage
Verify no users are currently assigned to the role.
2
Reassign Users
Move affected users to appropriate alternative roles.
3
Confirm Deletion
Permanently remove the role from your system.
Permission System Architecture
- Permission Hierarchy
- Permission Dependencies
- Permission Validation
Organized Permission Structure:Benefits:
- Logical grouping of related permissions
- Easy to understand and assign
- Scalable permission structure
- Clear hierarchy for dependencies
Atomic Permission Control
Complete Customization: Roles are built permission-by-permission. You start with zero access and add only the specific permissions needed. No permission bundles or packages - just individual atomic permissions you select.
Real-World Atomic Examples
Real-World Atomic Examples
Customer Support Representative:
- ✅ View customers
- ✅ Update customer information
- ✅ View transactions
- ✅ Process refunds
- ❌ Delete customers
- ❌ Create products
- ❌ Manage API keys
- ✅ View transactions
- ✅ Access financial reports
- ✅ Export transaction data
- ✅ View customers (for analysis)
- ❌ Process refunds
- ❌ Edit customers
- ❌ Manage products
- ✅ View products
- ✅ Manage inventory
- ✅ Edit product information
- ❌ Delete products
- ❌ View transactions
- ❌ Access customer data
- ✅ View products
- ✅ Edit product information
- ✅ View customers (for campaigns)
- ✅ Export customer data
- ❌ Manage inventory
- ❌ Process transactions
- ❌ Delete anything
Permission Independence
Permission Independence
Key Principle: Each permission operates independently. You can:
- Grant “View Customers” without “Edit Customers”
- Allow “Create Products” without “Delete Products”
- Enable “View Transactions” without “Process Refunds”
- Provide “Export Data” without “Delete Records”
- Mix read permissions across all categories
- Combine write permissions selectively
Building Custom Access Patterns
Building Custom Access Patterns
Start from Zero: Every new role begins with no permissionsAdd Selectively: Choose only the permissions that match the user’s actual job needsMix Categories: Combine permissions from different areas as neededRefine Over Time: Add or remove individual permissions as roles evolve
Role Assignment Strategies
Department-Based Roles
Create roles that match organizational departments and their specific needs
Function-Based Roles
Design roles around specific job functions regardless of department
Level-Based Roles
Establish roles that reflect seniority and responsibility levels
Project-Based Roles
Temporary roles for specific projects or initiatives
Build roles atomically by selecting individual permissions to create precise access control that matches your exact business needs and team responsibilities.