Control API access by restricting requests to specific IP addresses. IP whitelisting adds an extra layer of security by ensuring only trusted locations can access your Devdraft API, protecting against unauthorized access.
What is IP Whitelisting?
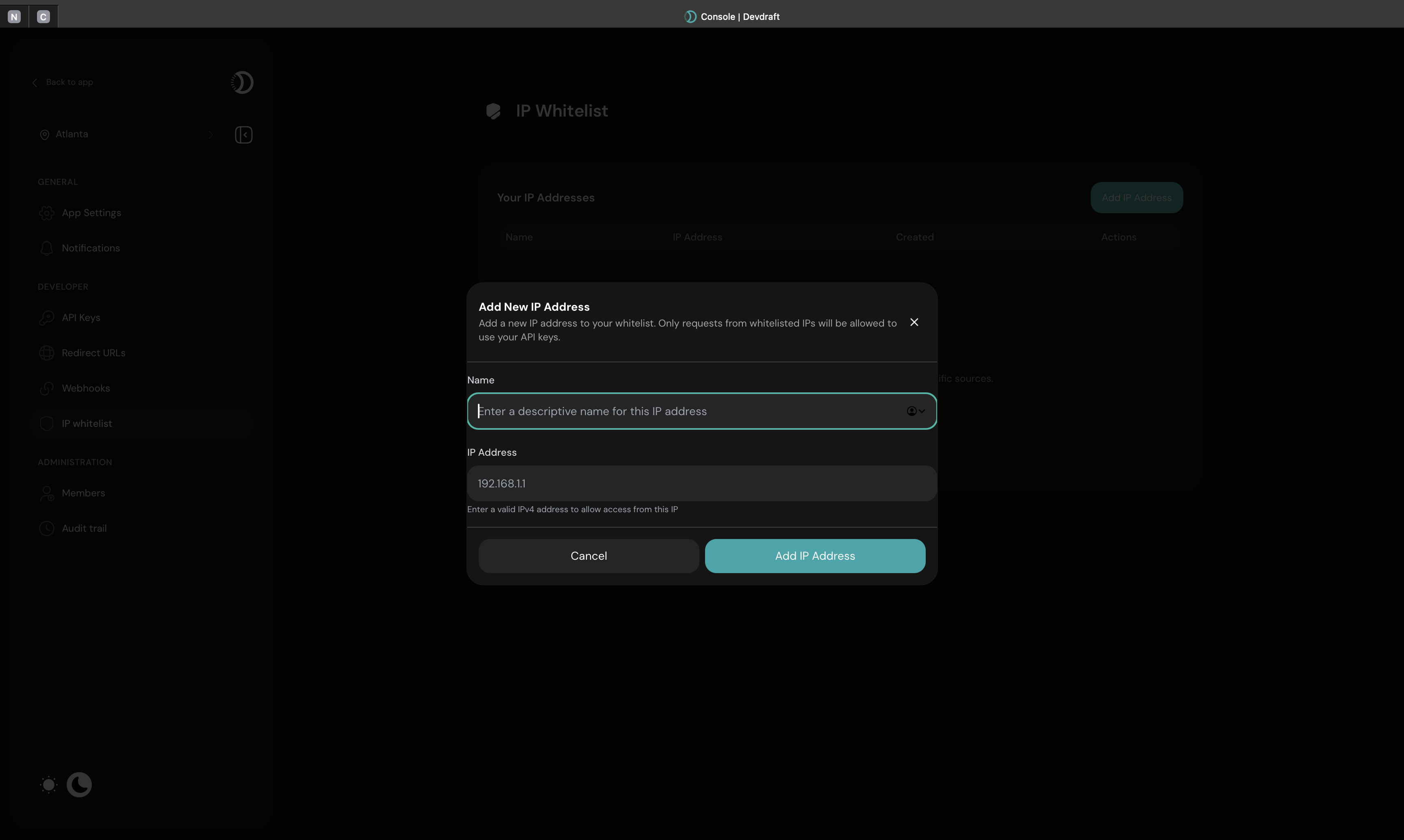
IP whitelisting is a security feature that restricts API access to requests coming from pre-approved IP addresses. This adds an extra layer of protection by ensuring that only specified IP addresses can authenticate and make requests to your Devdraft account.
Add IP Address Interface
Quick Setup
Set up IP whitelisting in under 3 minutes:1
Access IP Whitelist Settings
Navigate to App Settings → IP Whitelisting in your dashboard
2
Add IP Addresses
Click Add IP Address and enter the IP you want to whitelist
3
Configure Entry Details
Provide a descriptive name and verify the IP address format
4
Activate Protection
Save your IP whitelist to immediately restrict API access
IP Address Formats
- Single IP Address
- IP Range (CIDR)
- Multiple Entries
Individual IP Address:
- Format:
192.168.1.100 - Allows access from one specific IP
- Most restrictive option
- Perfect for fixed server locations
Adding IP Addresses
1
Access IP Whitelisting
Navigate to App Settings → Security → IP Whitelisting.
2
Add New IP Address
Click Add IP Address and enter the details:
- IP Address or CIDR range
- Description for identification
- Access level (optional)
3
Verify and Save
Confirm the IP address format and save the entry.
Managing IP Entries
View IP Whitelist
View IP Whitelist
Whitelist Overview:
- All configured IP addresses and ranges
- Entry descriptions and labels
- Creation dates
- Last access times
- Status (Active/Inactive)
- Edit IP entries
- Remove IP addresses
- Temporarily disable entries
- Add new IP addresses
Edit IP Entries
Edit IP Entries
Modify Existing Entries:
- Update entry names and descriptions
- Change IP addresses or ranges
- Modify access permissions
- Track change history
1
Select Entry to Edit
Click the edit button next to the IP entry you want to modify.
2
Update Information
Modify the name, IP address, or other details as needed.
3
Save Changes
Confirm your changes to update the whitelist immediately.
Remove IP Entries
Remove IP Entries
Security Management:
- Remove outdated or unused IP addresses
- Clean up old development environments
- Revoke access for former team members
- Maintain current whitelist accuracy
Monitor IP Activity
Monitor IP Activity
Access Tracking:
- Last request timestamps
- Request volume per IP
- Blocked access attempts
- Security event logging
Common Use Cases
- Production Servers
- Office Networks
- CI/CD Pipelines
- Development Environments
Server-to-Server API Access:
- Whitelist your production server IPs
- Include backup and failover servers
- Add load balancer IP addresses
- Consider cloud provider IP ranges
Best Practices
Document All Entries
Maintain clear descriptions for each IP entry to track purpose and ownership
Regular Reviews
Periodically review and clean up unused or outdated IP addresses
Test Before Production
Test IP restrictions in staging environments before applying to production
Monitor Access Logs
Regularly check access logs for blocked requests that might need whitelisting
Implementation Considerations
1
Plan Your IP Strategy
Before Implementation:
- Identify all systems needing API access
- Document current IP addresses and ranges
- Plan for IP changes and network updates
- Consider redundancy and failover scenarios
2
Test Thoroughly
Validation Process:
- Test API access from all whitelisted IPs
- Verify blocked access from non-whitelisted IPs
- Test edge cases and network configurations
- Validate backup and disaster recovery scenarios
3
Monitor and Maintain
Ongoing Management:
- Monitor for legitimate requests being blocked
- Track changes to your network infrastructure
- Update whitelist when systems change
- Review access patterns regularly
Security Considerations
Network Address Translation (NAT)
Network Address Translation (NAT)
Behind NAT/Firewall:
- Identify your public IP address
- Consider shared IP addresses
- Account for dynamic IP changes
- Plan for ISP IP rotation
Cloud Service Providers
Cloud Service Providers
Cloud Infrastructure:
- Use cloud provider IP ranges when available
- Consider elastic IP addresses
- Plan for auto-scaling scenarios
- Document cloud region specifics
VPN and Proxy Services
VPN and Proxy Services
Remote Access:
- Whitelist VPN server IPs
- Consider proxy service IPs
- Plan for VPN provider changes
- Monitor for IP conflicts
IP whitelisting provides strong access control but requires careful planning and maintenance. Ensure you have alternative access methods in case of IP changes or emergencies.